One type of attack that can be used using the ping commands can be the Denial of Service attack or DoS. A Denial of service attack is when “huge numbers of access requests [are sent] simultaneously to one website, which overloads that site's web server, thus preventing legitimate requests from being handled.” (Vahid & Lysecky, 2019). According to CloudFlare, some of the DoS attacks include flooding the target with ping requests, known as Ping Flood, or intentionally sending a ‘infected’ ping, known as the Ping Of Death (Cloudflare, n.d.). To do this, mostly the Ping Flood, it is commonly done using a variety of computers at the same time. That is a DDoS, or Distributed Denial of Service, where many computers have been infected and manipulated to execute this command. A computer becomes ‘infected’ when a virus enters the system, thus using the computer to spread and multiply, or executing spam commands (such a DoS), or obtaining information illegally.
A
virus can enter a computer system through various ways, clicking on a
suspicious email or link can be one such way. According to Cisco, “Spam email
is unsolicited and unwanted junk email sent out in bulk to an indiscriminate
recipient list.”. Because it is so common, most email services already have a
Spam or Junk folder to filter out these emails. It is these emails that, though
they might sound legitimate, make a computer system vulnerable to viruses. One
of the way you might noticed the virus is when your computer is running really
slow since the virus works in the background, coping itself and attaching the
copies to the emails and pings it makes the computer send out. A couple ways to
prevent this is to install anti-virus software to detect and isolate it, or
refrain from entertaining the suspicious email or link all together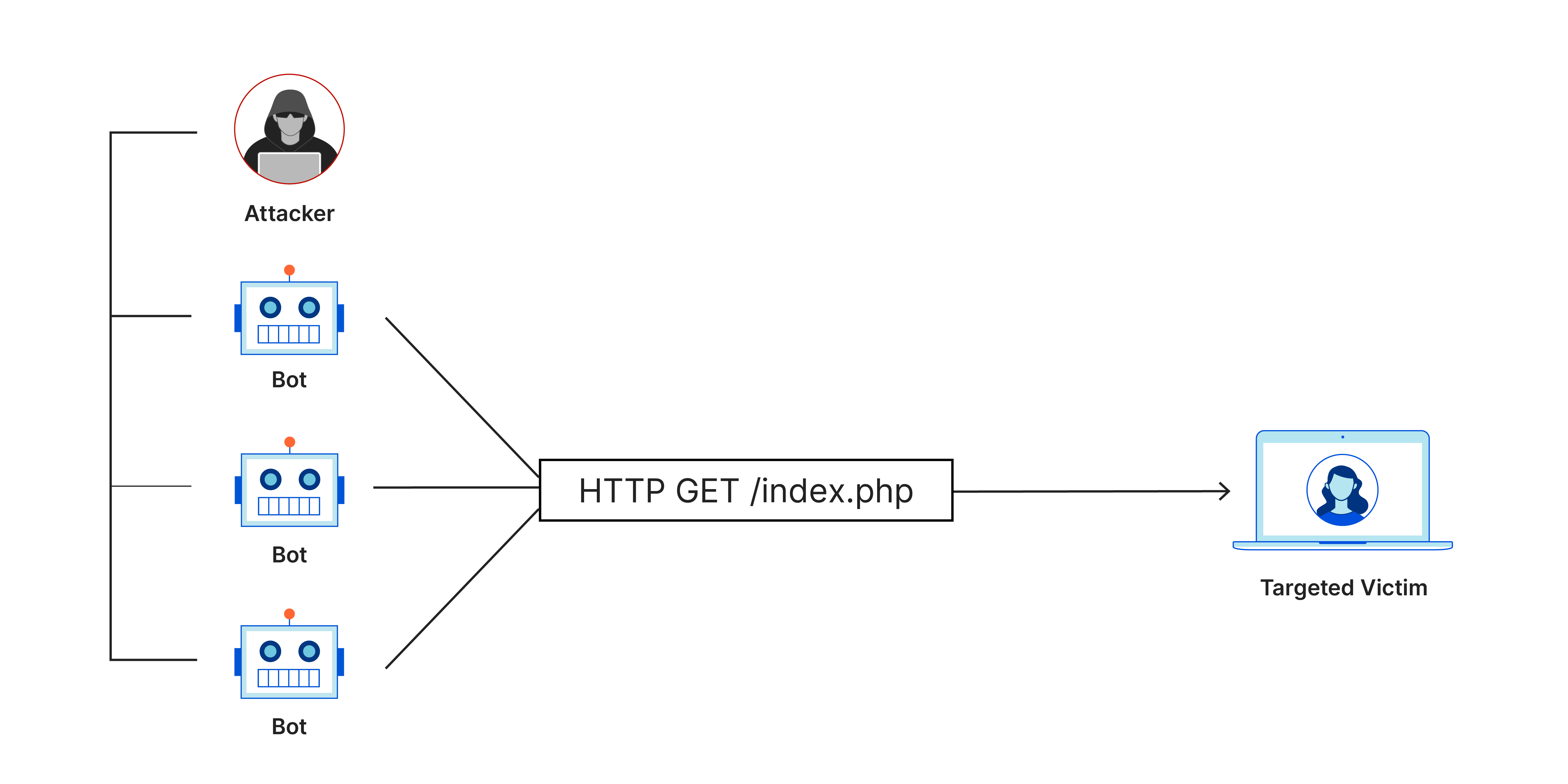
References
CloudFlare (n.d) What is a denial-of-service (DoS) attack https://www.cloudflare.com/learning/ddos/glossary/denial-of-service/
Cisco (n.d.) What is Spam Email? https://www.cisco.com/c/en/us/products/security/email-security/what-is-spam.html
Comments
Post a Comment